
Go Passwordless using FIDO2 with CyberArk Identity
Today’s Problem in Authentication.
In the age of information, Managing Passwords is a hectic task for all users, which leads to the practice of using the same password for all their accounts and sometimes even worse where users tend to use weak passwords like “<name>123”, “password” resulting in easy account hacks and breaches. Even if the service requires the users to change the passwords periodically, users start using patterns that are not recommended. Also, forgetting passwords and having to reset passwords frequently pulls down productivity.
This is where Biometric Authentication comes into play, which eliminates the need of managing huge lists of passwords.
CyberArk Identity FIDO2
CyberArk Identity MFA feature allows users the option to use the Local On-device authenticators such as Fingerprint, Windows Hello, and Mac Touch ID with a Zero-Trust factor on the service provider. Since CyberArk Identity offers public key encryption and makes use of data from local authentication it is a safer and more reliable way of storing passwords.
On-device authenticators can be either biometric or passcode, but here we are aiming to eliminate the need for passwords entirely. let’s understand more about the working of Biometrics and questions about its safety.
Biometric Authentication
Biometric Authentication is a security mechanism that relies on the unique biological characteristics of individuals to verify that they are who they say they are.
How does Biometric Authentication work?
Biometric authentication works by comparing two sets of data: the owner of the device and the actor trying to get access. If the two data are nearly identical, the device knows that “visitor” and “owner” are one and the same, and gives access to the person. This data that the system compares with is locally stored in the device which gives leverage and eliminates the need to trust the service provider.
How Safe is Biometric Authentication?
The Biometric Data is stored on the device like the iPhone’s Face ID and Windows Touch ID, this is much safer than storing it with the Service provider, even if the data is encrypted. Since CyberArk Identity follows Zero-Trust, Considering Biometric Authentication is the best fit for it.
Role of Zero-Trust in Passwordless Authentication
Zero-trust refers to an approach of validating every user, and every device before giving access to any data or asset even if they are inside the private network, which is a requirement in today’s IT infrastructure model where we need strict identity Verification for every person and device regardless of the network perimeter, they are in.
Here, In Biometric Authentication we might need to trust the device that is where CyberArk Identity offers the feature for Device authentication with FIDO.
The Key Components of Zero-Trust:
- User/application authentication
- Device Authentication
- Trust itself.
There are several Biometric authentication mechanisms like Face ID, Touch ID, iris scanning, etc over the years, but most of the mechanisms tend to have inconsistent security. But for enterprise apps, we need to make sure that there is strong security at every step in the employer’s device. This is where FIDO comes in.
Fast ID Online (FIDO)
FIDO is a standardized authentication protocol made with the purpose of eliminating passwords.
When the idea of using Biometrics instead of passwords for authentication was discussed in 2009, this inspired the idea of creating a standardized way of using public key cryptography and local authentication to enable Passwordless login.
The first version of FIDO was called FIDO U2F which was designed as a second-factor Authentication method. FIDO2 is the latest version that includes Web authentication and CTAP2, which strive to standardize and leverage strong authentication mechanisms on various devices like that Windows and Android.
Types of Protocol available
- Universal Authentication Framework (UAF)
- Universal Second Factor (U2F)
- FIDO2
How does FIDO2 work?
FIDO2 is built with two open Standards: FIDO Client to Authenticator and W3C WebAuthn.
These 2 works together to provide a Passwordless authentication experience. To provide this it may use some embedded auth-mechanics like biometrics or PINs or roaming authenticators like fobs or USB device.
When a user is trying to access an online Service for the first time, they will be prompted for a registration where the user provides a username and password. During this process a Public and Private key pair is generated.
The Private Key is locally stored in the device itself and associated with ID and domain of the online service, and the Public Key is stored in the online service’s Key Database and server.Each time a user attempts to access the online service, it uses the APIs to verify user’s credentials with the authenticators.
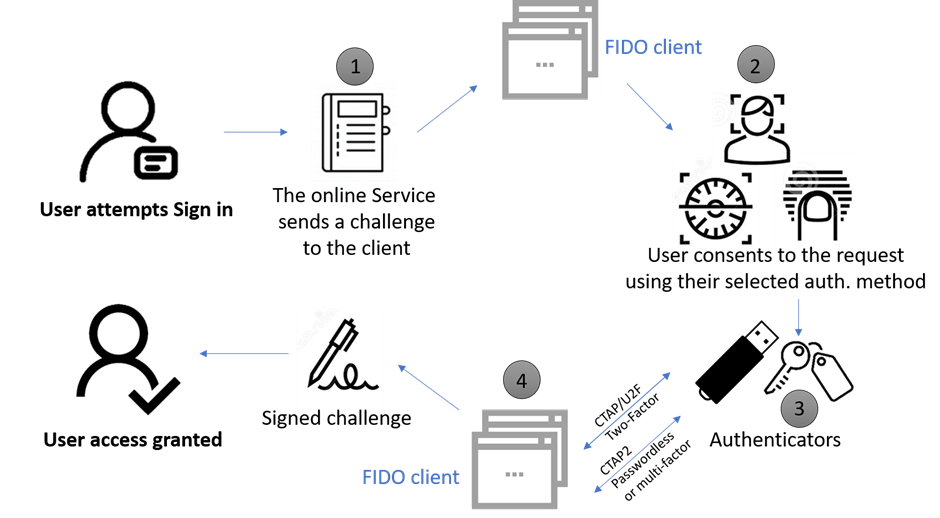

- When the user attempts to log in the FIDO2 server sends the FIDO client a challenge using WebAuthn, requesting to sign the data with the private key locally.
- Now the users use the biometric authentication that he/she chooses at the time of registration.
- The client obtains the private key from the authenticator. This can be the user’s computer, mobile, or an external piece of hardware.
- The client signs the challenge and proves the device is the one that possesses the private key.
Steps to Enable FIDO2 in CyberArk Identity
Requirements
- CyberArk Identity account with Admin Access
- A user using the Authenticator needs to have a device with a local authenticator like Windows hello, Mac Touch ID
Enabling FIDO2 authentication for a user
- Log in to Admin portal
- Go to Core Services > Policies
- Edit or Add a new Policy Set

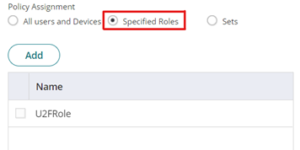
- Select a specific role under Policy Assignment

- Go to User Security policies > User Account Settings.
- Choose “YES” to Enable users to enroll in FIDO2 Authenticators.

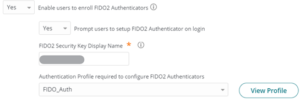
- The authentication profile is Optional, choose that as per requirement.
- Now save and Push Policy.
Enabling FIDO2 from CyberArk Identity UserPortal
- Log in to the User Portal
- Go to Account > Authentication Factors
- Click on Add for On-device Authenticator

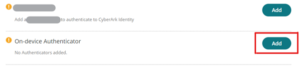
- Click on Next and Give a Name for your Authenticator like <TouchID>
- Verify with the widow’s security

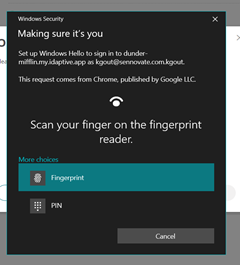
- The On-device Authenticator is “Configured Successfully” and Ready to use.
Now That the FIDO2 Authentication is set up from both ends we can implement on-device authentication for login as single or multifactor authentication for the user to specific access such as for login to the admin portal.
Have questions about finding an
Identity and Access Management consultant?
Call +1 (925) 918-6618 the consultation is free.
About Sennovate
Sennovate delivers custom identity and access management solutions to businesses around the world. With global partners and a library of 1000+ integrations, we implement world-class cybersecurity solutions that save your company time and money. We offer a seamless experience with integration across all cloud applications, and a single price for product, implementation, and support. Have questions? The consultation is always free. Email [email protected] or call us at: +1 (925) 918-6618.
