
Securing Access with Identity & Access Management (IAM) in Google Cloud
Understanding the Foundation of IAM in Google Cloud
- Identity and Access Management (IAM) is a fundamental security mechanism in Google Cloud.
- It ensures that only authorized users, services, or devices can access specific resources.
What is IAM?
- IAM (Identity and Access Management) lets you control who has access to your Google Cloud resources.
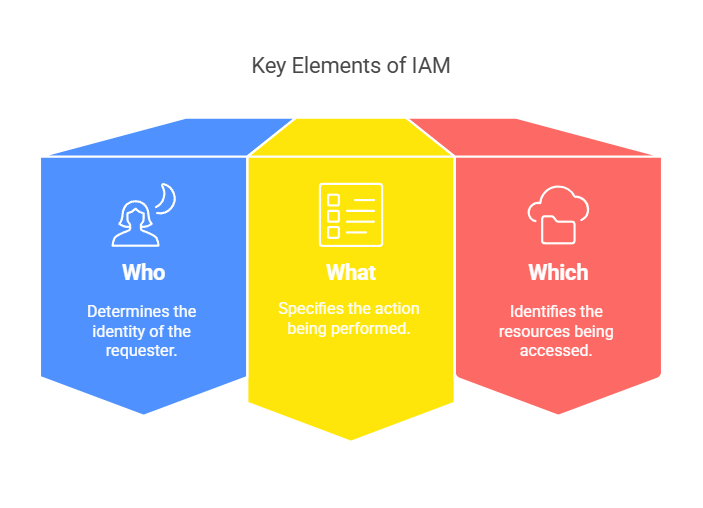
- IAM helps answer three critical questions
- Who (Identity) – Determines which users, services, or devices are making a request.
- What (Action)– Specifies the action being performed (e.g., listing storage buckets, creating a VM).
- Which (Resources) – Identifies the Google Cloud resources being accessed.

Key IAM Concepts in GCP
Members
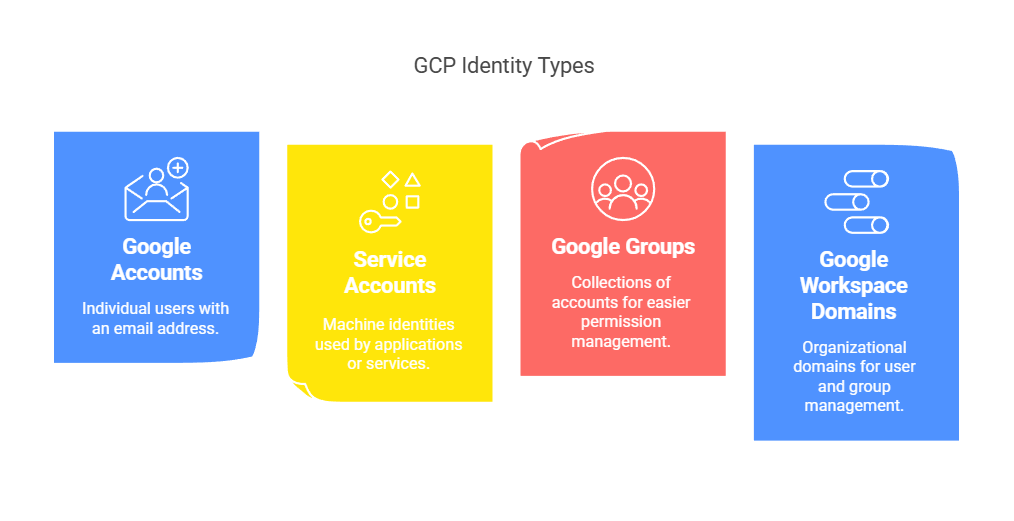
- Members are entities that can be granted permissions within Google Cloud. These include:
- Google Accounts
- These accounts are Individual users with an email address.
- Service Accounts
- These accounts are machine identities used by applications or services.
- Google Groups
- These are collections of accounts for easier permission management.
- Google Workspace (G Suite) or Cloud Identity Domains
- These domains are used for organizational user and group management.
- Google Accounts

Roles
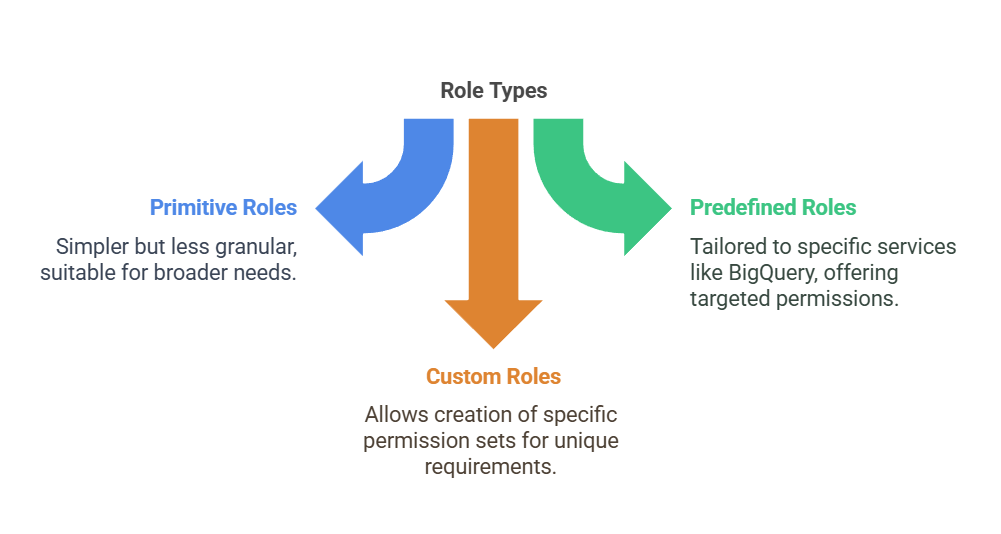
- Roles define what actions members can perform on resources.
- General Roles
- These are the original, broader roles in Google Cloud. They are simpler but less granular than other options.
- Predefined Roles
- Google provides a wide array of predefined roles tailored to specific Google cloud services. For example, roles/bigquery.dataEditor grants permissions to edit data within Big Query datasets.
- Custom Roles
- If both these options don’t suit your needs, then you can create custom roles. This allows you to define a very specific set of permissions.
- General Roles

IAM Policies
- IAM Policies use a structured format to define who has what access to which resources. Here is an example policy:
“bindings”: [
{
“role”: “roles/storage.objectViewer”,
“members”: [
“user:[email protected]”,
“serviceAccount:[email protected]”,
“group:[email protected]”
]
}
]

IAM Policy Hierarchy
- Organization
- This represents the top-level node, typically corresponding to a company or organization.
- Folders
- Folders allow grouping of projects for better management, especially in large enterprises with multiple departments.
- Projects
- Projects act as the boundary for resource management and billing, containing resources like VMs, storage, etc.
- Resources
- Resources are the actual cloud services and assets deployed within projects.


Want to protect your devices from cyber attacks but don’t know how to start with it?
No worries! Sennovate experts cybersecurity experts are just a call away.
