Fortify Your Cloud: Exploring GCP’s Security Tools
Google Cloud Platform (GCP) provides a robust suite of security tools to help businesses protect their cloud infrastructure. These tools address various facets of security, including threat detection, compliance, data protection, and user access control. Below, we will look at the key GCP security tools and their essential features.
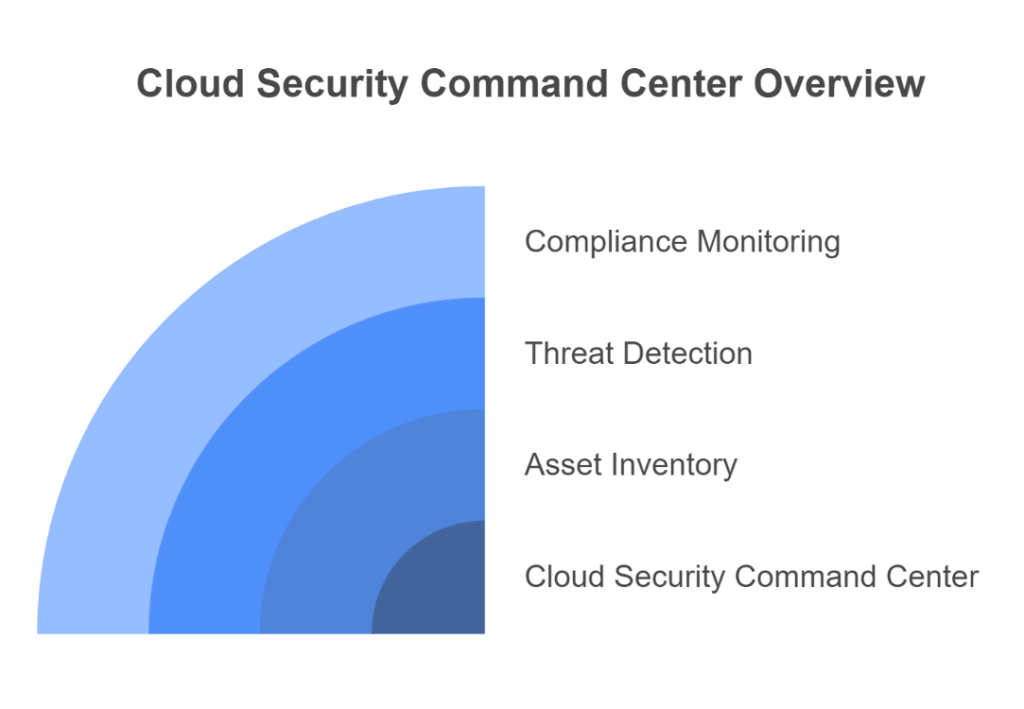
1. Cloud Security Command Center (Cloud SCC)
Cloud SCC serves as a centralized security dashboard for your GCP environment, offering comprehensive visibility into potential risks and simplifying their management.
Key Features Include:
- Asset Inventory:
Automatically generates an up-to-date inventory of your GCP resources such as virtual machines, databases, and storage buckets enabling you to identify unexpected changes quickly.
- Threat Detection:
Integrates with tools like:
- Security Health Analytics: Identifies vulnerabilities, misconfigurations, and compliance issues.
- Event Threat Detection: Detects suspicious activities, such as unusual logins or malware.
- Compliance Monitoring:
Checks your environment against standards like PCI DSS, HIPAA, and GDPR, simplifying audits and helping maintain regulatory compliance.

2. Cloud Armor
Cloud Armor is a web application firewall (WAF) that protects your online services against cyberattacks, including Distributed Denial of Service (DDoS) attacks.
Key Features Include:
- Custom Rules:
Tailor rules to defend against vulnerabilities like SQL injection or cross-site scripting (XSS).
- DDoS Protection:
Guards against large-scale and targeted attacks aimed at overloading your application.
- Adaptive Protection:
Uses machine learning to identify abnormal traffic patterns and block emerging threats in real time.

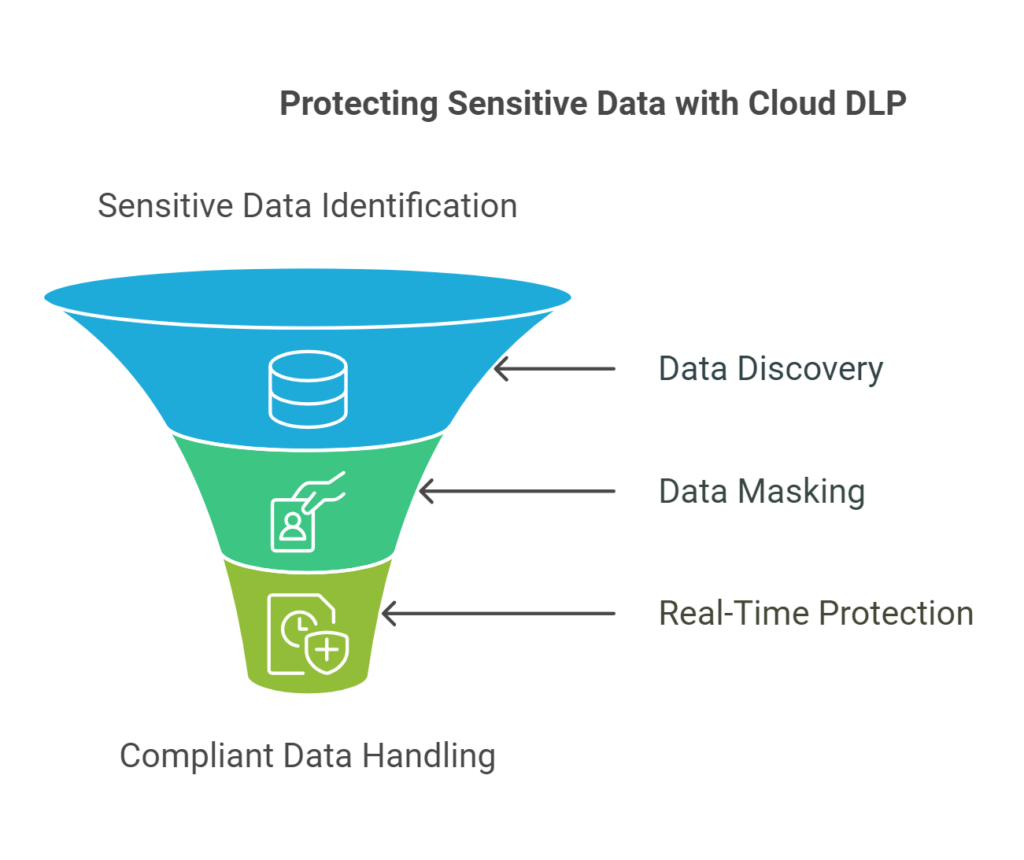
3. Cloud Data Loss Prevention (Cloud DLP)
Cloud DLP helps organizations discover, classify, and protect sensitive data such as personal information or payment details.
Key Features Include:
- Data Discovery:
Scans storage systems, logs, and databases to locate sensitive information like names, emails, and credit card numbers.
- Masking and Tokenization:
Anonymizes sensitive data through masking or encryption—replacing credit card numbers with tokens, for example, while preserving usability for analysis.
- Real-Time Protection:
Scans and redacts sensitive data in real time to maintain privacy compliance during processing.

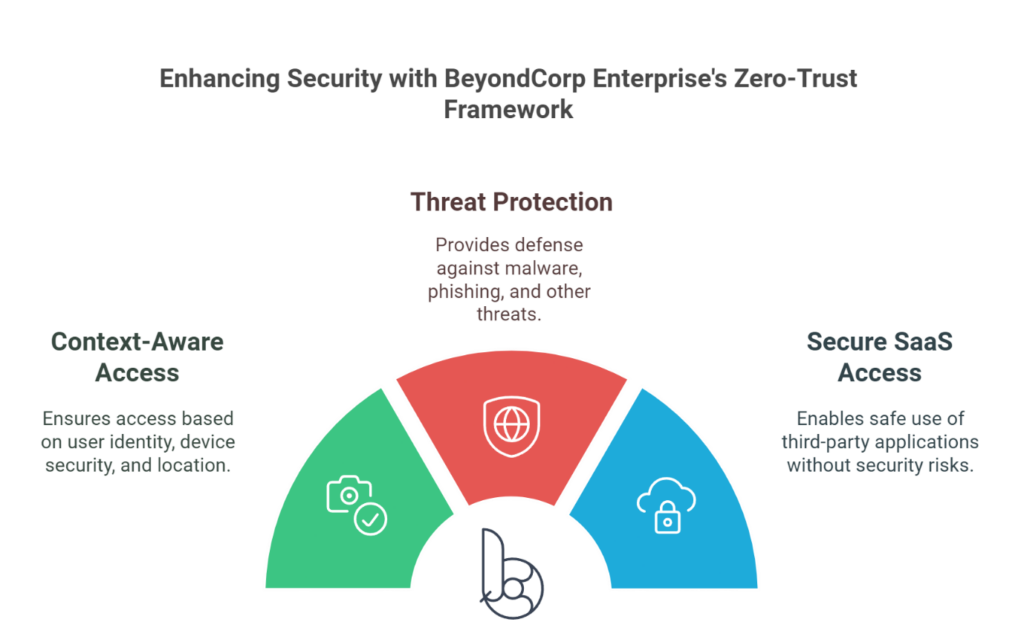
4. BeyondCorp Enterprise
BeyondCorp Enterprise is Google’s zero-trust security framework, designed to secure access without relying on traditional VPNs.
Key Benefits:
- Context-Aware Access:
Verifies user identity, device security, and location before granting access.
- Threat Protection:
Guards against malware, phishing, and other common threats.
- Secure SaaS Access:
Facilitates safe usage of third-party applications without compromising security.


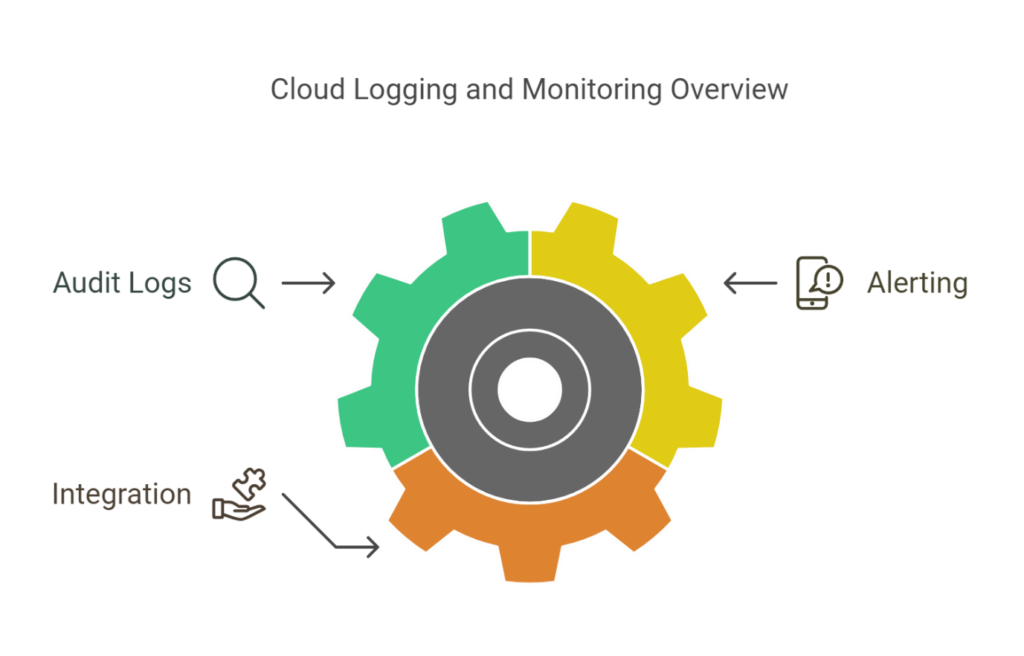
5. Cloud Logging and Monitoring
Cloud Logging and Monitoring provide real-time insights into the health and security of your cloud environment.
Key Features:
- Audit Logs:
Tracks every action in your environment, simplifying investigations into suspicious activities and supporting compliance.
- Alerting:
Sends notifications for unusual events like unauthorized access or unexpected changes.
- Integration:
Works seamlessly with third-party tools like Splunk or Elastic for deeper analysis.

Want to protect your devices from cyber attacks but don’t know how to start with it?
No worries! Sennovate experts cybersecurity experts are just a call away.



