

Securing Your Cloud Infrastructure: Best Practices for Building a Robust VPC Network
- In today’s world of cloud computing, securing your network is more critical than ever. Google Cloud’s Virtual Private Cloud (VPC) offers a powerful solution to protect your resources and ensure secure communication between various components of your infrastructure. Let’s take a closer look at the key elements that make VPC a vital tool in your cloud security strategy.
VPCs: The Backbone of Secure Cloud Networks
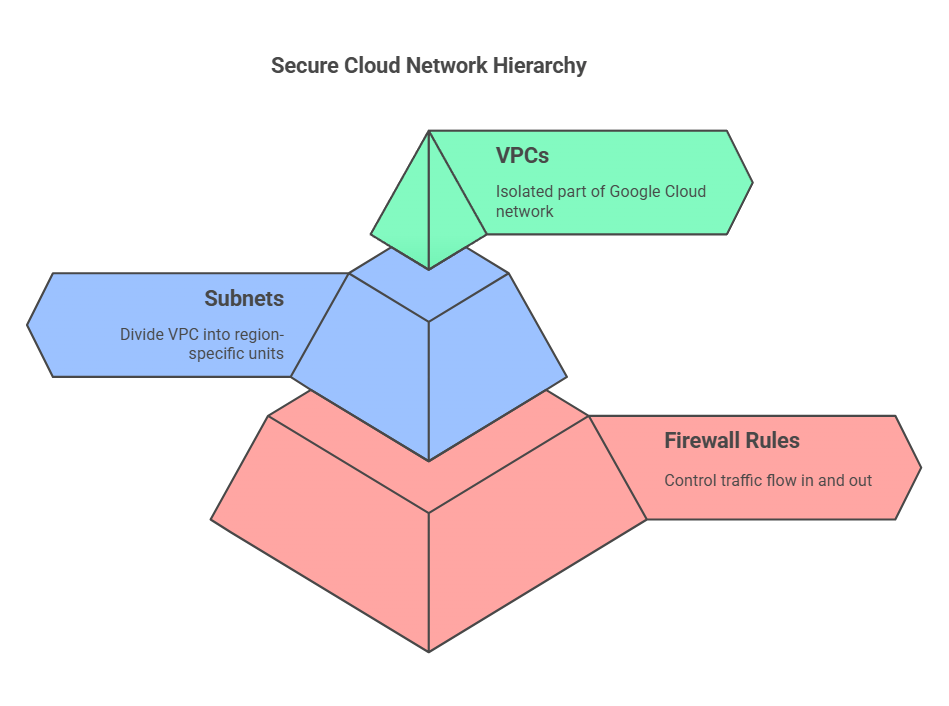
- A VPC functions as a dedicated, isolated part of the Google Cloud network, giving you the flexibility to customize your infrastructure. It enables you to build scalable and secure network architectures without exposing your resources to the public internet.
Global Scope
- VPCs span multiple regions, allowing you to deploy applications and services globally without direct exposure to the public internet.
- This geographic flexibility means you can optimize performance and availability while maintaining tight control over who can access your resources.
- For example: If you’re running a global e-commerce platform, and you need to ensure that your website performs well for customers all around the world. Then, with a VPC that spans multiple regions, you can deploy your application in different geographic locations, such as USA, Germany, and Singapore, to serve users from those regions.
Subnets and Regional Isolation
- A VPC can be divided into smaller units called subnets, which are tied to specific regions. This means that you can have separate subnets for different geographic locations, like one in North America, another in Europe, and another in Asia.
- The benefit of this geographic isolation is that you can separate different types of services into different subnets.
- For example: You might place your production services in one subnet, your development services in another, and your testing services in yet another. This way, even if one subnet is compromised, the others remain isolated and secure.
Firewall Rules
- Firewall rules act as your first line of defence by controlling the flow of traffic in and out of your VPC.
- These rules work at the IP and port levels, meaning you can specify what types of traffic are allowed to enter or exit your network based on the source and destination IP addresses, as well as the specific ports involved.
- By carefully defining these rules, you can adopt a deny all approach, where all traffic is blocked by default. From there, you can explicitly allow only the necessary traffic that your applications or services require.
- For example: You might allow HTTP traffic (port 80) for a web server but block all other incoming traffic unless it’s from a trusted source, such as your internal network or a VPN.

Routing
- Routing in a VPC is crucial for managing how traffic flows within your network and how it interacts with external systems such as the Internet.
- VPC allow you to define custom routes to control the flow of traffic between different subnets and out to the public internet. This ensures that services within your VPC communicate in a secure and efficient manner, following only the approved paths you define.
- For example, you might want traffic from your web servers (public-facing) to go through a load balancer before reaching application servers (private). You can set up routes to make sure this happens and prevent unwanted traffic from getting into your internal network.
Designing for Security
Segmentation
- Divide your VPC into logically isolated subnets. A common approach is using a tiered architecture that isolates different layers of your application. For example, you might have separate subnets for the Frontend (Web) Tier, Application Tier, and Backend (Database) Tier.
Least Privilege
- A core principle of cloud security is restricting access. Apply a deny all policy by default and selectively open ports and protocols as necessary for your services. This minimizes the risk of unauthorized access.
Defence in Depth
- Don’t rely solely on firewalls for security. Incorporate multiple layers of defence, such as Identity and Access Management (IAM), encryption, and network monitoring to protect your resources from various types of threats.
Visibility
- Tools like Cloud Logging and VPC Flow Logs offer full visibility into your network activity. This helps you monitor traffic patterns and quickly identify any anomalies that could indicate a security breach.


Best Practices
- Use separate VPCs for development, testing, and production environments. This keeps production systems isolated from less secure, experimental environments.
- Prioritize using private IPs within your VPC to ensure resources remain isolated from the public internet. For services that need internet access, use secure options like load balancers or Identity-Aware Proxy (IAP). This approach minimizes attack surface.
- If you manage multiple projects, consider using a Shared VPC. This centralizes network administration and reduces security risks by ensuring consistent policies across all projects.
- Cloud environments evolve rapidly, and so should your security posture. Regularly audit your firewall rules, network configurations, and IAM policies to ensure they remain aligned with best practices.
Want to protect your devices from cyber attacks but don’t know how to start with it?
No worries! Sennovate experts cybersecurity experts are just a call away.



