
The Rise of Quantum Computing: How It Impacts Cybersecurity & Encryption.
Quantum computing is set to transform various industries, ranging from drug discovery to financial modelling. Nevertheless, this innovative technology also poses a significant threat to contemporary cybersecurity. In contrast to classical computers, quantum machines are capable of solving intricate mathematical problems at speeds millions of times faster, which could render existing encryption techniques ineffective.
For businesses in the USA and across the globe, it is essential to comprehend the implications of quantum computing on cybersecurity, encryption, and data protection. In this blog, we will examine:
✔ How quantum computing undermines traditional encryption
✔ The imminent “Harvest Now, Decrypt Later” (HNDL) risk
✔ Solutions in post-quantum cryptography
✔ How Sennovate’s cybersecurity services in the USA can assist organizations in their preparations.
- Understanding the Mechanism of Quantum Computing and Its Impact on Cybersecurity
The Strength of Qubits Compared to Classical Bits
Conventional computers operate using bits (0s and 1s), whereas quantum computers utilize qubits, which can be in multiple states at once (quantum superposition). This capability enables them to: – – A. Execute parallel computations at remarkable speeds.
B. Break encryption algorithms at a rate significantly faster than supercomputers.
Shor’s Algorithm: The Threat to Encryption
In 1994, mathematician Peter Shor demonstrated that a quantum computer could:
✔ Compromise RSA and ECC encryption (employed in banking, healthcare, and governmental systems).
✔ Decrypt secure communications (SSL/TLS, VPNs, military data).
📌 Current Situation: Google and IBM have already showcased quantum supremacy—indicating that the risk is no longer merely theoretical.
2. The “Harvest Now, Decrypt Later” (HNDL) Threat
What Is HNDL?
Cybercriminals and state-sponsored hackers are currently pilfering encrypted information, fully aware that they will be able to decrypt it once quantum computing becomes widely available.
Who’s at Risk?
Financial institutions (encrypted transactions)
Healthcare providers (patient records)
Government agencies (classified intelligence)
Critical infrastructure (power grids, defense systems)
📌 Example: In 2023, the NSA issued a warning that China is accumulating encrypted US data for potential future decryption.
How Long Until Quantum Attacks Become Reality?
Optimistic Estimate: 5-10 years (2030+)
Pessimistic Estimate: Sooner, if advancements accelerate
Key Takeaway: Organizations need to take immediate action to safeguard their long-term data.
3. Which Encryption Methods Are Vulnerable?
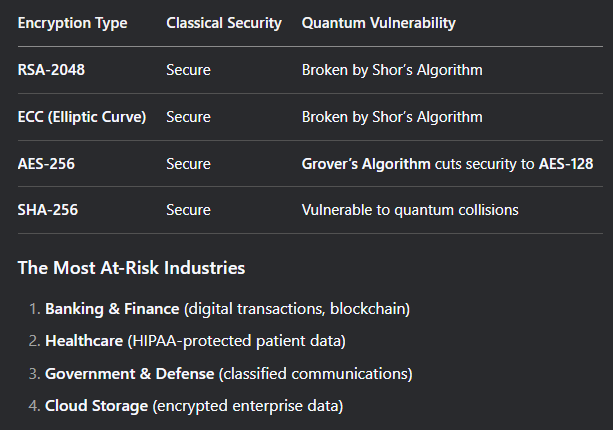

- Post-Quantum Cryptography: The Solution
What Is Post-Quantum Cryptography (PQC)?
PQC denotes encryption algorithms that are resistant to quantum attacks, specifically designed to endure the challenges posed by quantum computers.
NIST’s Post-Quantum Standardization (2024 Update)
The National Institute of Standards and Technology (NIST) is in the process of finalizing standards for quantum-safe encryption, which include:
✔ CRYSTALS-Kyber (Key encapsulation)
✔ CRYSTALS-Dilithium (Digital signatures)
✔ Falcon & SPHINCS+ (Alternative signature schemes)
How Businesses Can Prepare Today
Inventory Sensitive Data – Determine which data requires protection at the quantum level.
Adopt Hybrid Cryptography – Integrate classical encryption with quantum-resistant methods.
Upgrade PKI Systems – Get ready for the transition to PQC.
Partner with Quantum-Security Experts – Such as Sennovate’s cybersecurity services based in the USA.
- How Sennovate Assists Organizations in Staying Ahead
As a premier provider of cybersecurity services in the USA, Sennovate delivers:
✅ Quantum Risk Assessment – Detect weaknesses in your encryption.
✅ Post-Quantum Cryptography Migration – Adopt NIST-approved algorithms.
✅ Zero Trust + Quantum-Ready Security – Safeguard against future threats.
✅ Compliance Alignment – Fulfill forthcoming NIST, CMMC, and FIPS 140-3 standards.
📞 Obtain a Complimentary Quantum Security Consultation – Protect your data before it is too late!
The Quantum Cybersecurity Era Is Approaching
Quantum computing is set to transform cybersecurity permanently. While it presents significant advantages, it also poses risks to global encryption standards. Organizations must:
✔ Evaluate quantum risks immediately
✔ Shift to post-quantum cryptography
✔ Collaborate with specialists like Sennovate to secure future defenses
Do not delay for the quantum revolution—prepare now.
